Definition of forensic and digital forensics
Forensic Science
Two main groups of people allowed to speak to a judge:
- witnesses, allowed only to present what they saw/heard, but no interpretation allowed.
- experts, allowed to present information/facts/documents, and provide interpretation of those facts.
Forensic Science aims to collect evidence and make an interpretation of the facts, and then present a report to the court.Forensic Science is the application of science to criminal and civil laws, mainly—on the criminal side—during criminal investigation, as governed by the legal standards of admissible evidence and criminal procedure.
Forensic scientists can work in both criminal and civil cases; can work for either the prosecution or the defence
Digital Forensic
Digital Forensic is a branch of Forensic Science that encompasses the recovery and investigation of material found in digital devices, often in relation to computer crime.
Why we need digital forensic?
- Cyber crime and cyber enabled crime is flourishing
- The integrity of electronic system is vulnerable
- Professional & business reputations are exposed
- Computer Crime defects our trust of using digital devices, hence interoperability(流通性) and transaction is harmed
Knowledge field of digital forensics
IT Security: Security for protection - develop tools and procedures to protect the information
Digital Forensics: Prosecution or Defense - discover all the facts related to computer crime
Overlap of these two fields: System hardening(make system more secure and possible for digital forensics scientists to find solid evidence.)
Definition
Live Forensics, Network Forensics, Computer Forensics, Mobile Forensics, Database Forensics
Scientific tasks, techniques, and practices used in the investigation of stored or transmitted binary information or data for legal purposes. ISO/IEC 30121
“the process of identifying, preserving, analysing and presenting digital evidence in a manner that is legally acceptable”
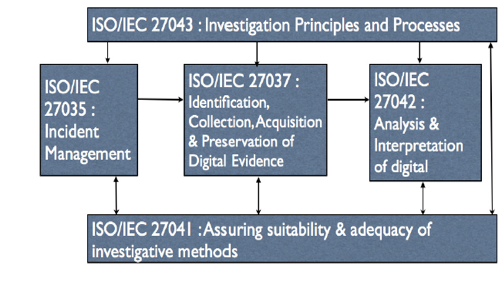
Steps in a Digital Forensic Examination
- Acquire evidence
- Analyse evidence
- Produce report(must have a specific standard to be accepted in the court)
-Provide ‘Expert’ consultation and testimony
Acquisition
Before starting a search, we must get a search warrant & search order.
Evidence collection
- Collection & digital search on site
- Overt: inform the owner about the search
- Covert: without informing the owner that the search has been conducted (does not often happens)
- Bring the device to the lab to do the search
Search Warrants
Who may issue a search warrant?
- Judge of high court, can be asked by two groups of people:
- law enforcement departments, e.g. police based on a suspicion of crime.
- private organization/person: “someone committed a crime against us (e.g. issued a false documentation and harmed our benefit) and we believe there is some evidence in their device that support our claim.” This is called a “search order”
- National security organisation, they can do search without getting a permission (but must apply for a warrant after the search)
High priorities in issuing warrants:
- Scope of the warrant: the data may not even in the country if the data is saved in cloud services, the warrant might not be able to be issued because of country boundary.
- Legal privilege issues: Search must be committed only to search for related evidence related to the crime and cannot do anything else. e.g. if an organization is accused for financial crime, but the forensic specialist find evidence of illegal immigration, forensic specialist should not report anything about the immigration fraud without a relevant warrant.
- Impact on the running of the business: if forensic specialist take away their device, there might be big influence on the organisation. We should be aware of this and minimise the impact.
If device is located away from boundary, a search warrant cannot be issued.
Search warrant must identify where the device is located, and the specialist is only allowed to search for the device on the site outlined by the warrant.
What are we acquiring?
Digital information that is accessible from:
- hard drives:
- the most popular type of hard drive used to come with a high-speed rotating disk and a magnetic head. Don't have a short access time. - now there is a dramatic shrink in size of hard drives. Electronic hard drives have faster access time. - usb sticks
- mobile phones
- cameras
- CDs, DVDs, Tapes … etc
A Copy and a Clone/Forensic Image
If someone clicks “delete” on a file, the link/reference to the file is deleted, but the information is still on the hard disk.
If you order a usual “Copy” you only get referenced files. But if you do a “Clone”, you can possibly get access to deleted files that could provide valuable information.
A forensic image must have a digital signature: Only digitally signed image can be used in court as trusted digital evidence that has not been tampered with/changed in the process of copying and evaluation.
Acquisition process
- Digitally photograph evidence items: demonstrating the evidence comes from specific device in specific location.
- Formally document evidence items
make sure the chain of command is not broken, the devices are never left unattended from the beginning of the search.
- Acquire evidence item onto ‘sterile drive’
sterile drive was never written into. need device to block changes to the sterile drive
- Verify ‘digital signature’ of acquisition
Evidence case file
Copy all images to single (sterile) case drive.
Specialised Hardware/Software
- Two tools used:
- Encase
- FTK Imager
- Write-blocking hardware to ensure that the subject item is not written to
- Blocking software to stop writing into the original software
Write Blocker
A write blocker is any tool that permits read-only access to data storage devices without compromising the integrity of the data. NIST‘s general write blocking requirements hold that: - The tool shall not allow a protected drive to be changed
- The tool shall not prevent obtaining any information from or about any drive
- The tool shall not prevent any operations to a drive that is not protected.
There are physical and logical write blockers that do the same task but in a slightly different way.
Acquisition hardware: a (write-blocking) device that connects the investigated device and the sterile drive.
Computer Forensic Software
Two different approaches to searching
- Encase: Just search
- FTK: Generation of index before search
- before the search, it tries to index any combination of terms used in the device. The generation of the index takes long time, but then search is extremely quick.
Depending on you need, you may use one of or both software tools.
- before the search, it tries to index any combination of terms used in the device. The generation of the index takes long time, but then search is extremely quick.
Analysis (Search)
What we are looking for:
- documents
- emails
- pictures
- who was on the system and when
- who copied what off the system and when
- who deleted what and when
- who created/modified what and when
- was the system time messed with
Report Production
Paper or DVD? Many judges don’t understand the capability of modern devices.
A matter of scale: if we have 200 gigabytes of data, presenting them on paper could stack to 50 times height of sky tower.
Admissibility
The deliverable in digital forensic is the report.
The report must be produced in a compliant fashion.
Admissibility is the acceptance of the report as evidence.
The NZ Evidence Act 2006 normalized that
Consider also “Rules of the Court”
Digital Forensic Issues
Expert Witness
Judicature Act 1908 N0 69 (as at date): Expert Witness Code of Conduct
- Expert witness duty to the Court:
- An expert witness has an overriding duty to assist the Court impartially on relevant matters within the expert’s areas expertise.
- An expert witness is not an advocate for the party who engages the witness.
- Code of Conduct:
- If an expert witness believes that his or her evidence or any part of it may be incomplete or inaccurate without some qualification, that qualification must be stated in his or her evidence.
- If an expert witness believes that his or her opinion is not a concluded opinion because of insufficient research or data or for any other reason, this must be stated in his or her evidence.
An expert witness, according to high court rules:
- Must have read and agreed to the High Court code of conduct for Expert Witnesses
- May give an ‘OPINION’ in evidence
- Is there to assist the Court. Does not act as an advocate for prosecution or defence
Search Warrants: very modern problem
Traditionally search warrants are issued to enter premises.
With the ICT architecture and cloud services, the data can be stored far away in location.
Safe guards the court is looking for:
- Independent Digital Forensics Consultant
- Personal undertakings to the court regarding actions
- To be aware of the impact on the business
- To hold information remote from plaintiff
- As an expert witness to act on behalf of the court (as per the undertakings re an expert witness)
Qualifications, Training, Experience & Ethics
Must have:
- Formal Qualifications (degrees, usually degree in business or CS)
- Training certificates Encase & FTK
- Wide & detailed experience in IT industry
- Legal procedure understanding
- Business experience
- Personal integrity
- Credibility as an Expert witness (Professional Indemnity insurance)
Indemnity Insurance
You may make a mistake that result in you being charged by the party harmed with your opinion about the case. If you are a professional in this field, it is almost obligatory to have the indemnity insurance to cover this risk.
Practical issues during search
Don’t just look for the obvious digital storage devices
Devices could be disguised/ very small: PC in a cardboard box, credit card camera, watch, USB drive in a barbie
Future trends
- Larger Storage devices
- More Information
- More (and more) mobile data
- The Cloud
- Evolving legal issues – Case Laws